Two-Factor-Auth (2FA)
Two-Factor-Auth (2FA) is available on BlueOnyx and can add as additional protection layer to SSH logins as well as for GUI logins.
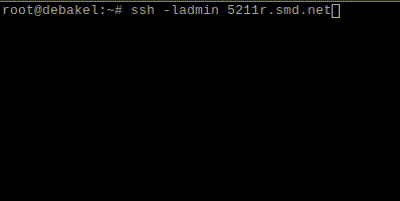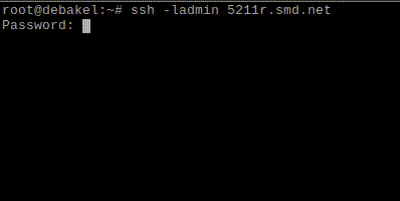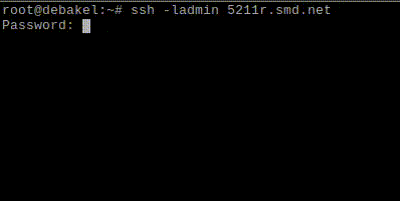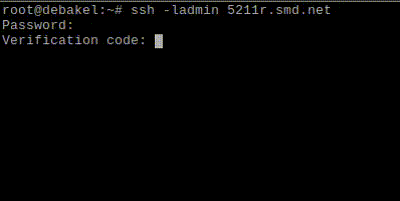
Our implementation of 2FA adds an additional layer of security to SSH enabled Shell accounts (and the GUI - on 5211R/5212R). If an account has 2FA enabled, then during login the user will be asked for the username, the password and additionally a one-time-use "Verification Code" that you can generate in a 2FA application on your mobile device. Supported 2FA authenticator applications are the Google Authenticator and the RedHat FreeOTP app, which are both available for Android and Apple devices. Download links for these apps are below.
2FA for SSH:
2FA for GUI logins:
 |
Authenticator usage:
- Download the Google Authenticator or the RedHat FreeOTP Authenticator app from the Apple App Store or Google Play Store.
- Open the app and tap the "+" button to add a new account.
- Select "Scan barcode" and on the BlueOnyx GUI page "Personal Profile" / "SSH Access" scan the QR code "2FA QR-image" or enter the "Authentication Key" manually.
- When logging in to the BlueOnyx server via SSH enter your username and password as well as the verification code generated by the Authenticator app.
- To ensure the security of your account, do not share your key or one-time codes with anyone.
Authenticator App Download Links:
|
Google Authenticator: |
|
RedHat FreeOTP Authenticator: |
 |
|
 |
 |
|
 |
GUI Integration in BlueOnyx (for SSH)
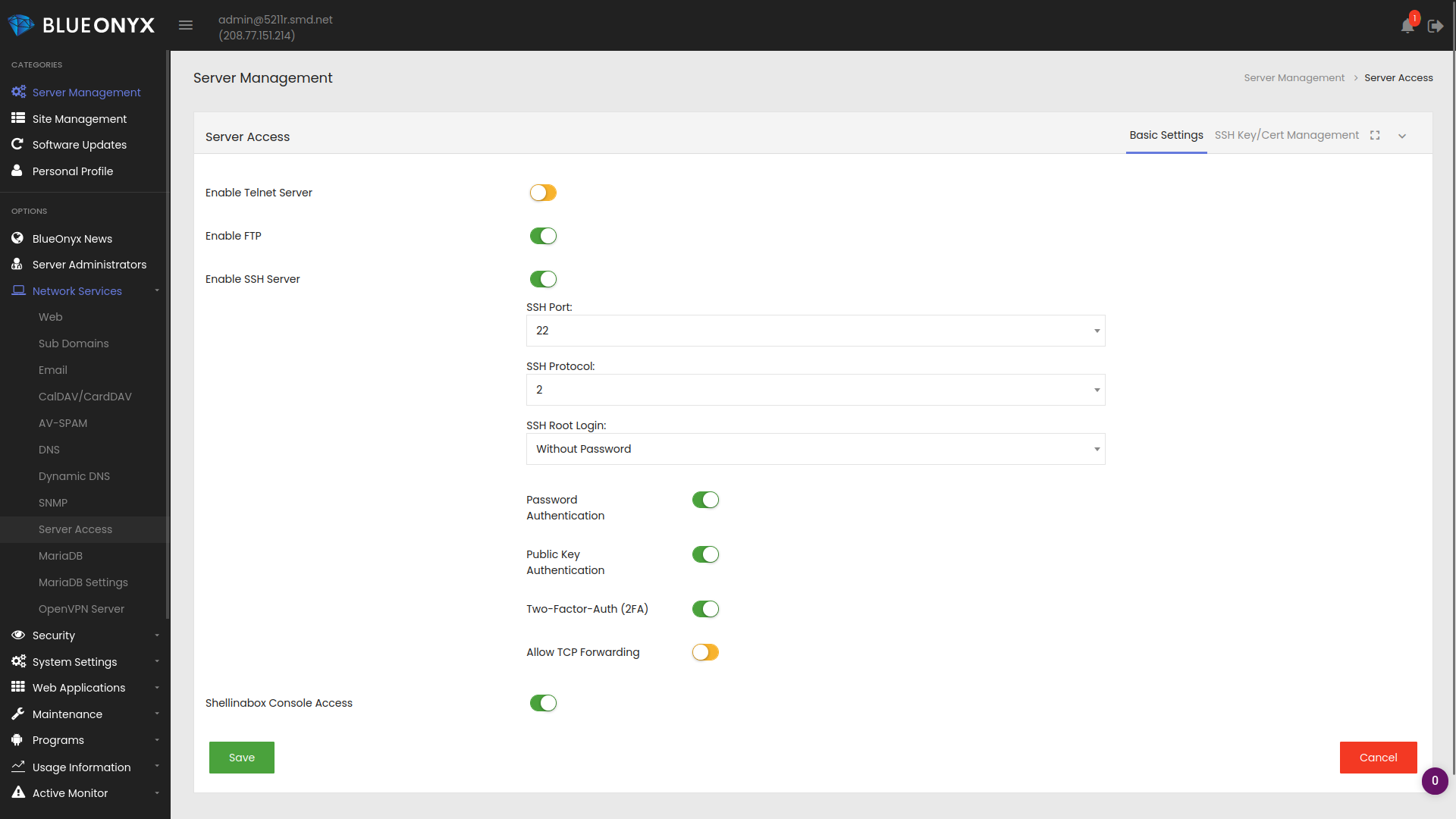
The server administrator needs to enable "Two-Factor-Auth (2FA)" under "Server Management" / "Network Services" / "Server Access". Please note that you may turn off "Password Authentication" and leave "Public Key Authentication" ticked. The way our 2FA integration works is this:
If a user has SSH keys exchanged, he can still login without password AND without 2FA. We consider exchanged SSH keys secure enough.
If a user doesn't have SSH keys exchanged, but has Shell access and has 2FA enabled? Regardless if "Password Authentication" is on or off: He will receive a username and password prompt and also the prompt to enter his 2FA key generated in the 2FA authenticator app.
If a user has Shell, 2FA is disabled for him and SSH is configured without "Password Authentication"? In that case login is only possible via exchanged SSH keys.
This way key exchange still works as before and 2FA can be used if a user doesn't have SSH keys exchanged yet.
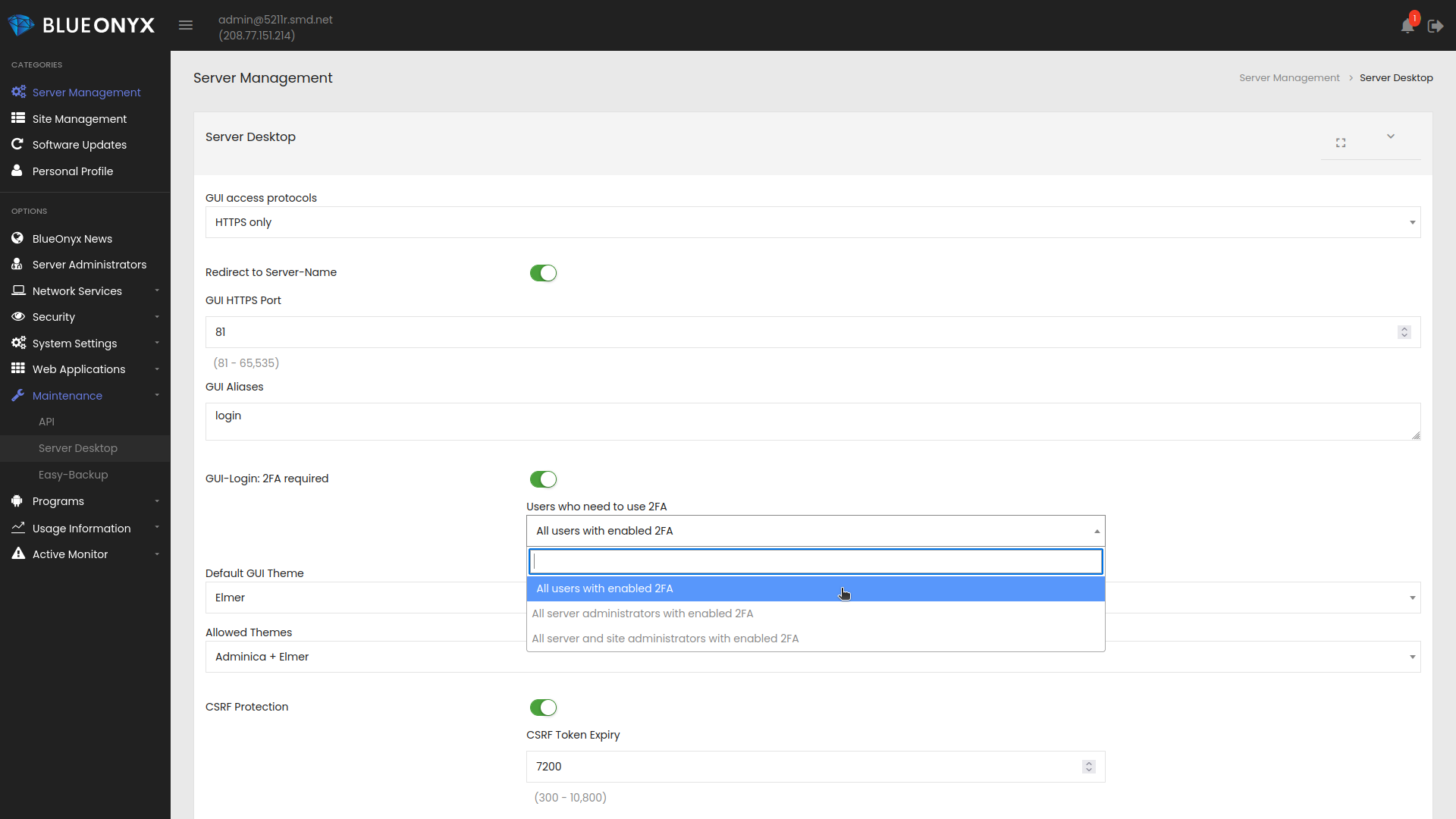
2FA as requirement for GUI Logins
Additionally the server administrator can configure the server so that certain users or all users are required to use 2FA for GUI logins. This can be done under "Server Management" / "Maintenance" / "Server Desktop":
2FA Vsite integration
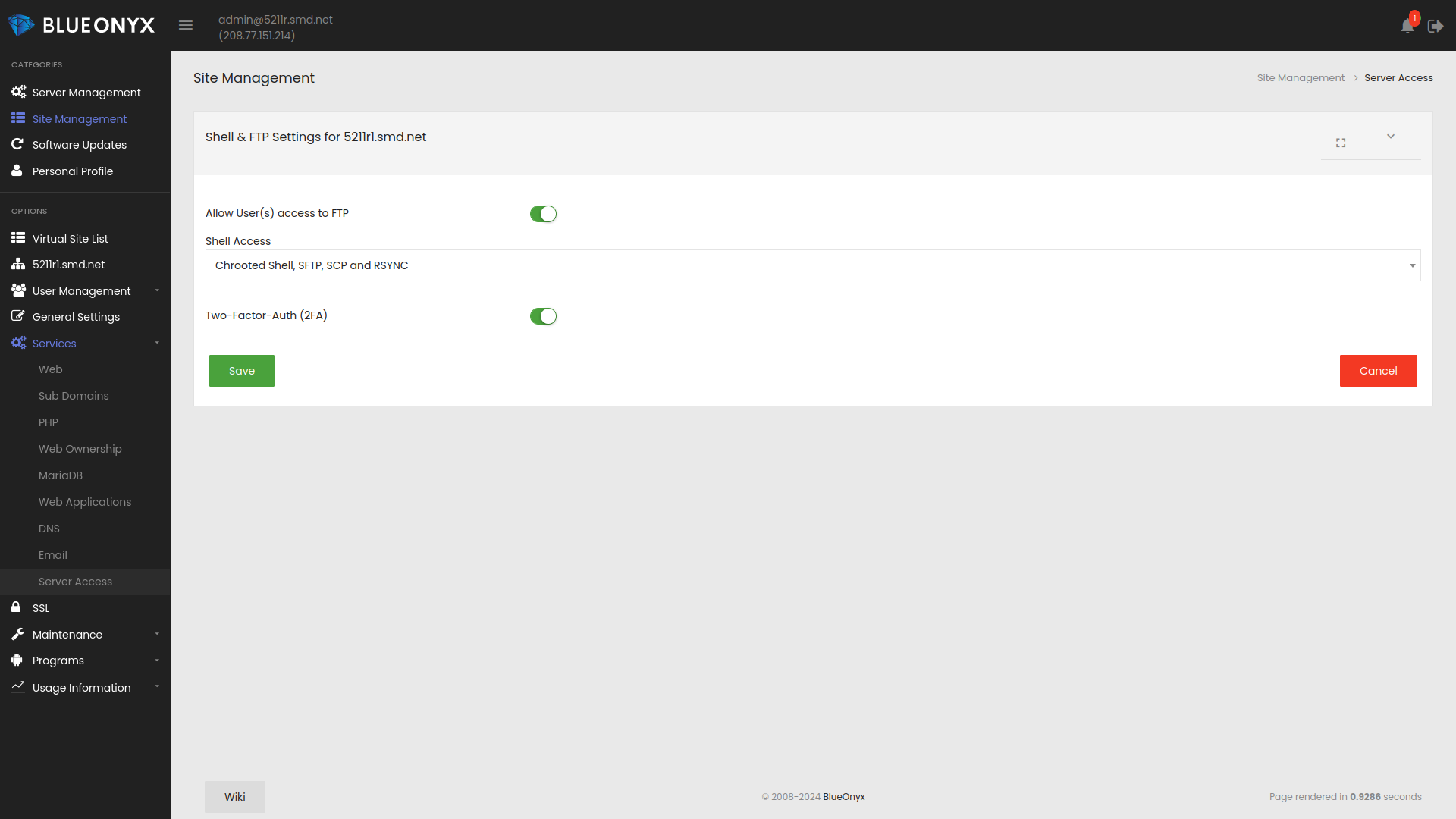
Each Vsite can have 2FA enabled or disabled for its users as shown below.
2FA User Management Integration
If a Vsite has 2FA enabled, each of its users automatically gets 2FA activated.
2FA Credentials for Users
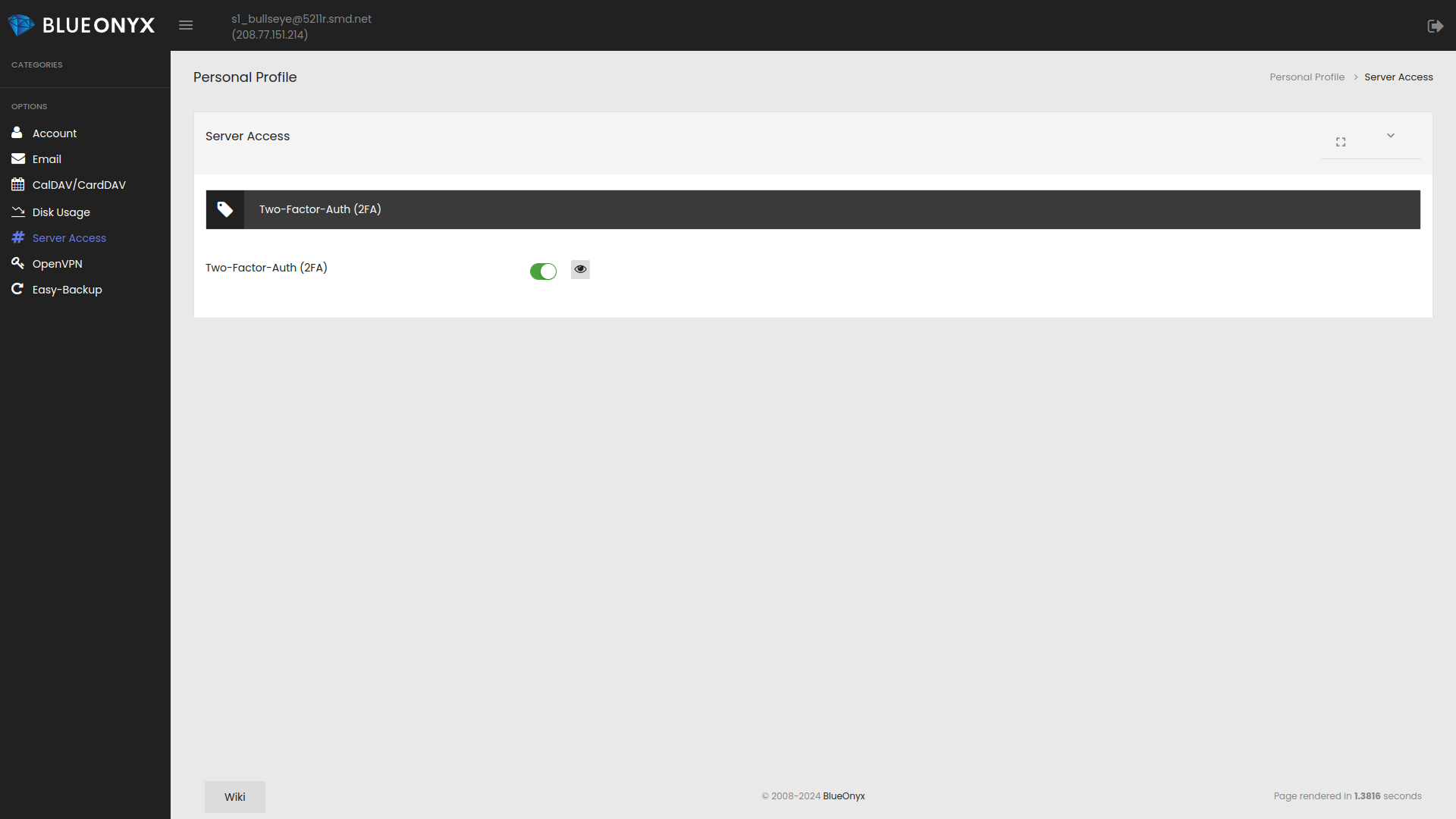
Each user can view his 2FA credentials in the GUI under "Personal Profile" / "Server Access" (siteAdmins) or directly under "Server Access":
By clicking on the icon with the eye symbol the 2FA credentials will be shown:
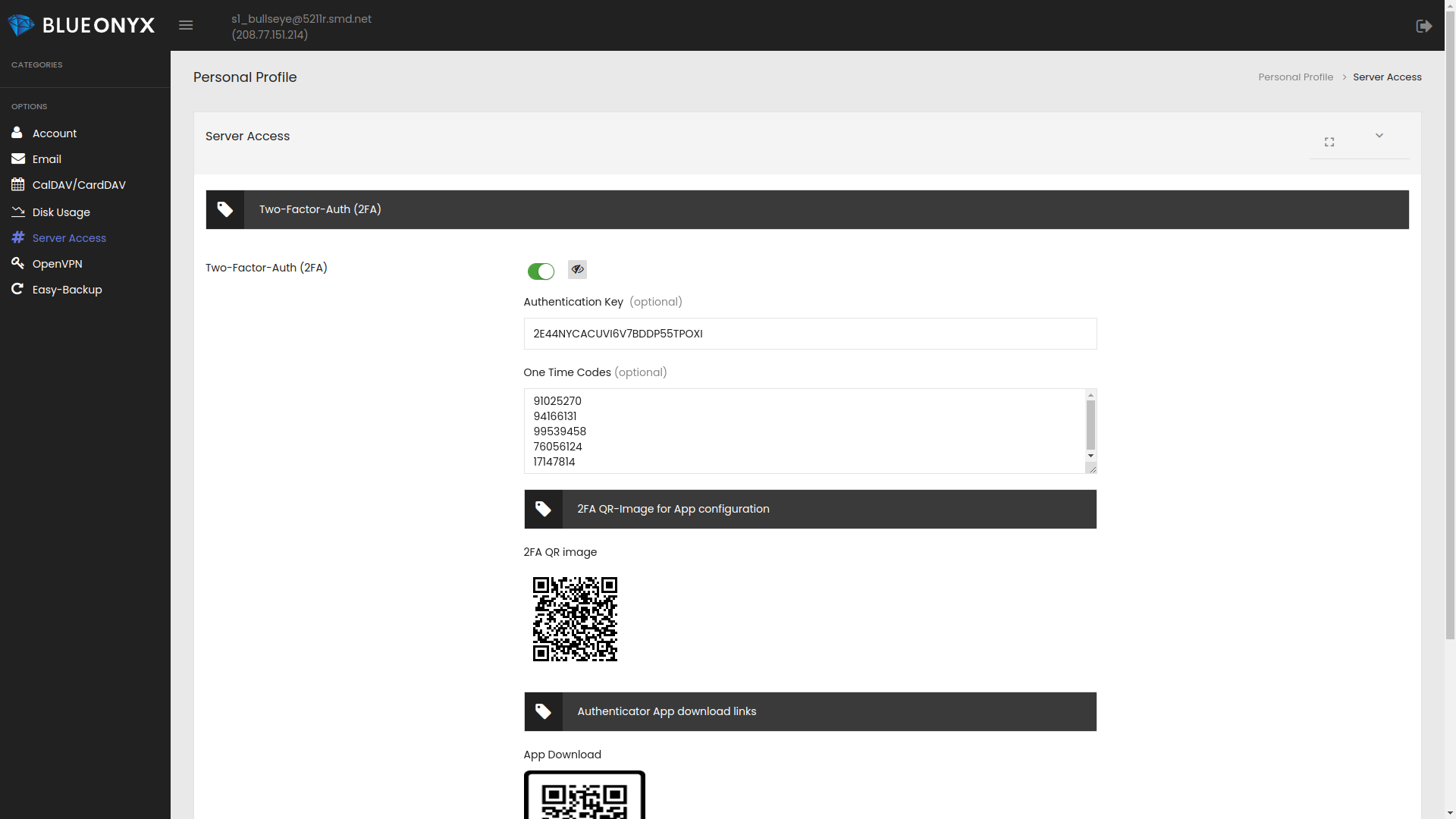
The "Authentication Key" can be used to manually configure an authenticator app, but the easiest way is by scanning the QR code with the authenticator application.
The "One Time Codes" shown on this GUI page can each be used once in case access to the authenticator application is not possible. Rhe "Authenticator Key", the "One-time-codes" as well as the QR image should be safeguarded with utmost precaution.
The "2FA QR image" is really all one typically needs. Open your 2FA application on your mobile device. This should either be the Google Authenticator app or the RedHat FreeOTP authenticator app. Click on the '+' button in the app to add an account, then click the QR icon in the app and point the camera of your mobile device to this QR-image. That will automatically configure your 2FA app with the details of this SSH account in order to provide 2FA one-time-codes, which you can then use during SSH logins.
This GUI page also another QR-image called "App Download". If scanned in a QR code reader (or by clicking on the "URL"-button instead) this page will open and the user can install the 2FA app of his choice by following the links to the respective appstore matching his device architecture.
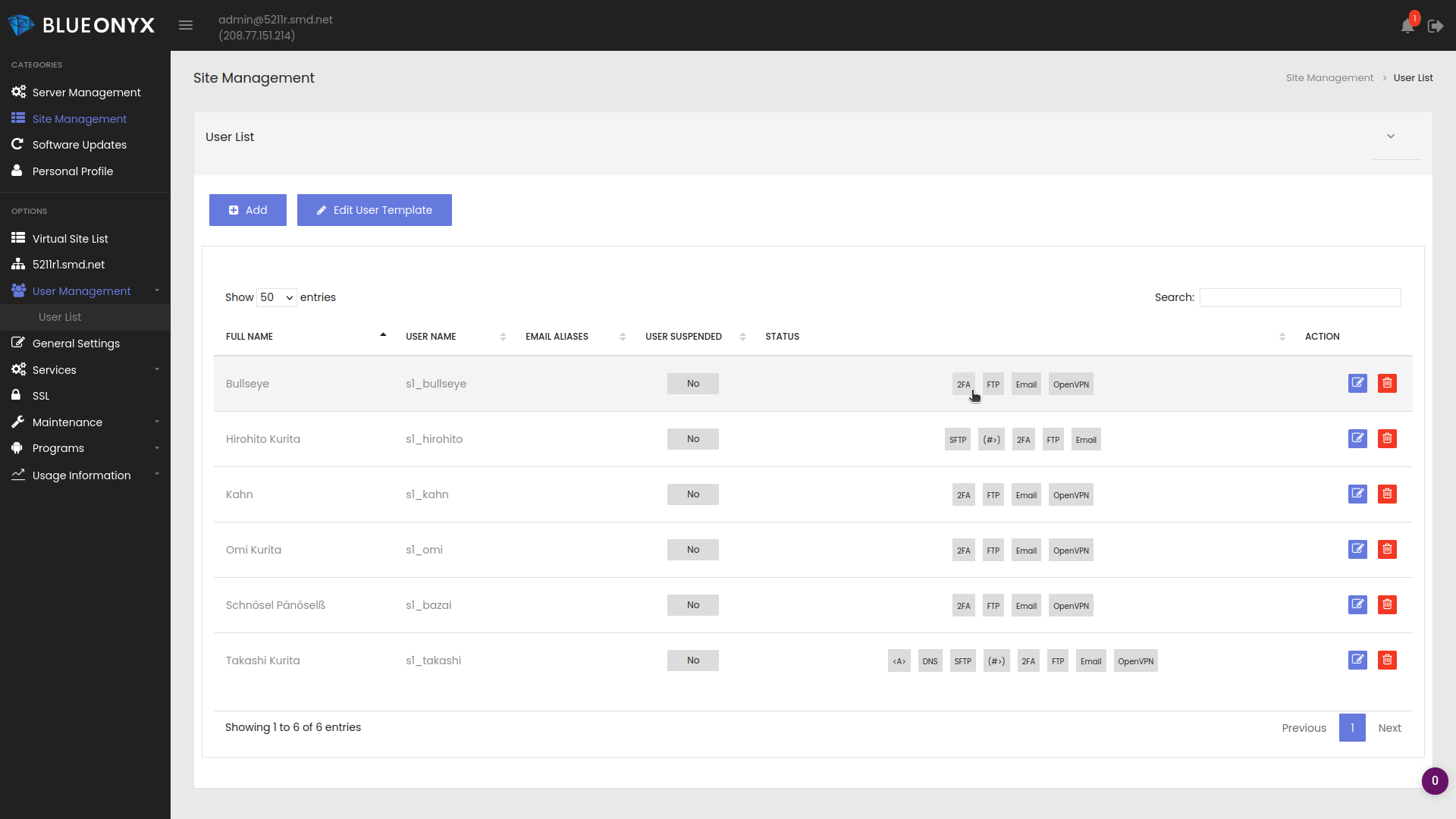
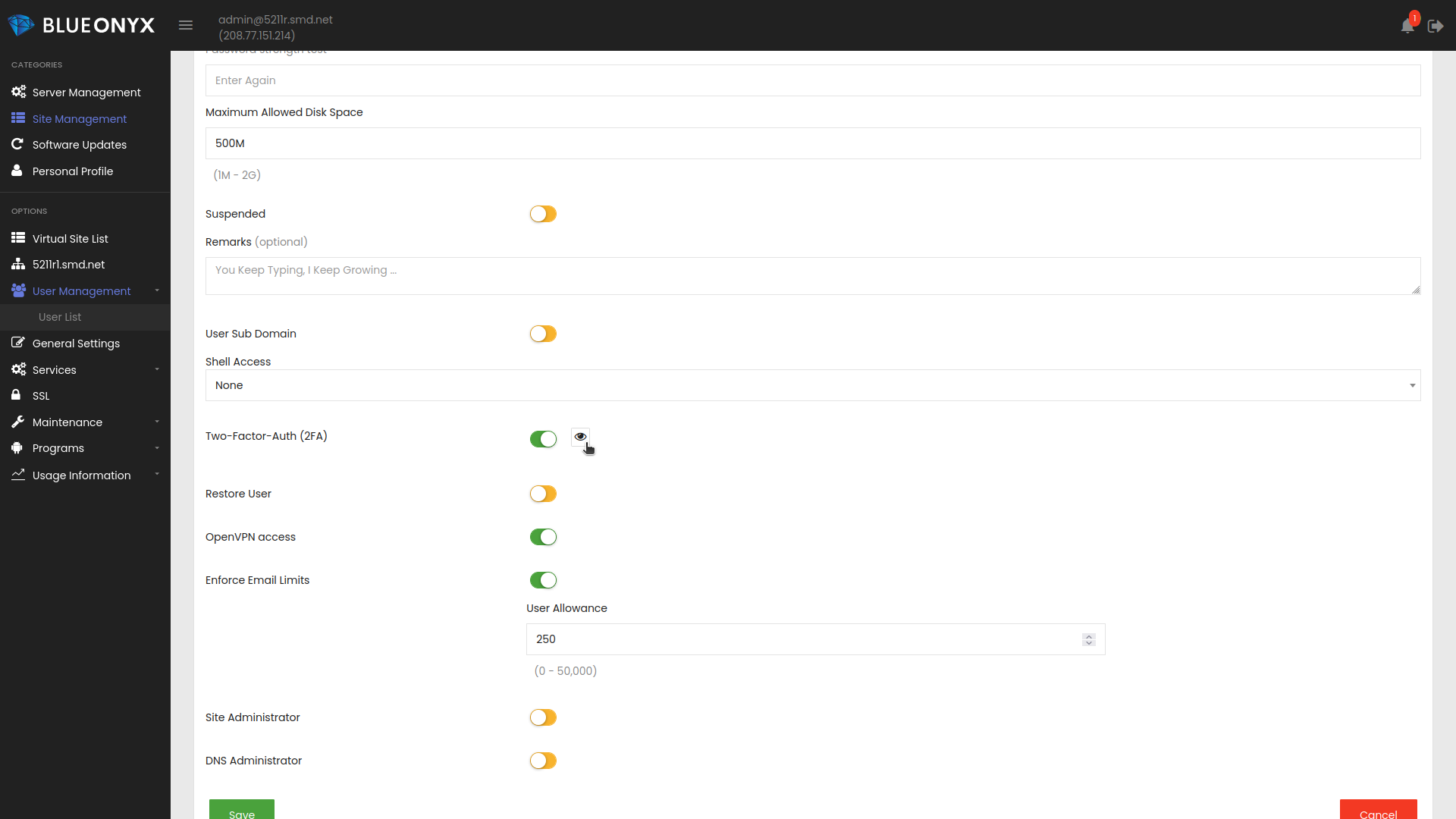
Server- and Site-Administrators can also view the 2FA credentials of their Users if the Vsite and Users have 2FA enabled:
All they need to do is to edit the user in question and to click on the "eye" icon next to the "Two-Factor-Auth (2FA)" enabler. Disabling the enabler (and saving the changes) will wipe existing 2FA login details of any given user. New 2FA login details will get generated when the feature is enabled again.